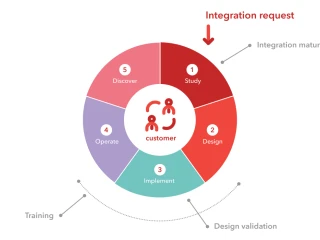
Integration: connecting the dots, keeping track of the whole
Now that all-in-one business suites are being replaced with best-of-breed IT landscapes, solid integration between business applications is more important than ever. A systemic approach based on technical and strategic best practices is paramount to keep track of the whole.


/Aveve-720x360-(1).webp?mode=autocrop&w=320&h=240&attachmenthistoryguid=44eda048-2073-4faa-945f-d3744c03a8d1&v=&c=e3eb5c837858885d8de11aad9be73a719cfaead2ef4e91436c96948e0cbe8837)
/720x360-The-first-S4HANA-Public-Cloud-implementation-in-Asia-(1).webp?mode=autocrop&w=320&h=240&attachmenthistoryguid=d878d53e-64c1-4b2b-bcb4-868385a7f94c&v=&c=16b903519c0e9027169b386f139adb2dd76f56c2937d6a4b7074a1d7ca35bd8f)

/Woman-holding-laptop-(1).webp?mode=autocrop&w=320&h=320&attachmenthistoryguid=303eed2f-b0b5-4631-a1e6-418dc46b9f8f&v=&c=77d19c7054c9ba7e9756eae92dfb383f4969f646df0eca03be993aac2d7568da)



